
Risk, Compliance, and Resilience
Today’s organizations face a range of technological and strategic challenges that are more complex and dynamic than ever before. Security compliance has become increasingly important and continues to be the primary factor guiding decisions about risk and security programs. Risk management is vital to ensuring trust among customers, employees, and strategic allies and is also an indicator of how well an organization can carry out its mission and manage its future resources. 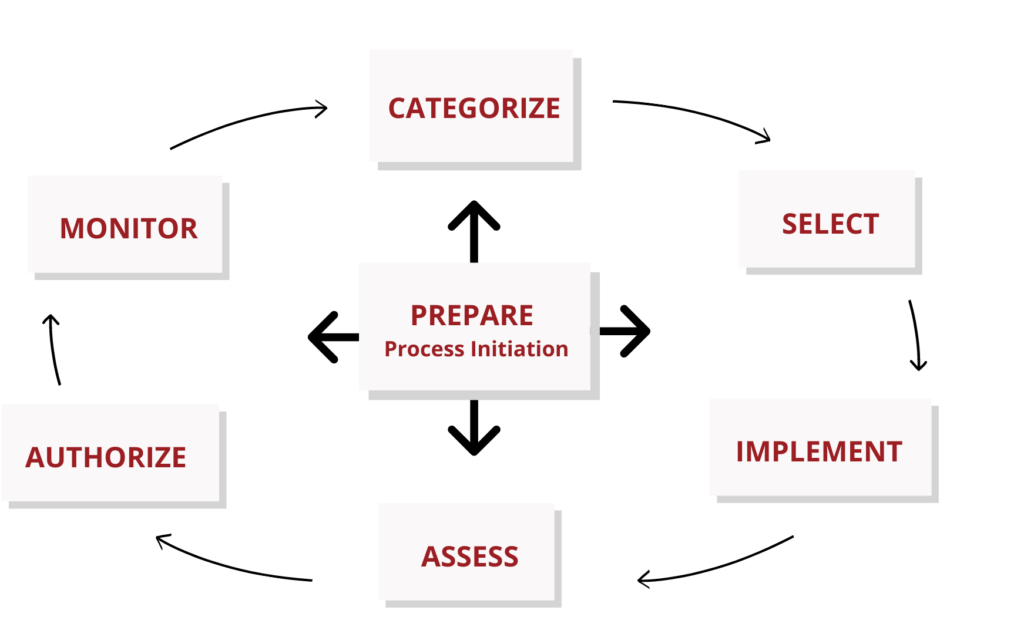
FusionPoint’s core capabilities are risk, compliance, and resilience services, and we devote all our resources to developing stronger solutions and expertise in these areas. Our goal is always to employ risk-based methodologies and recommendations that consider the different degrees of exposure and risk tolerances of our clients. FusionPoint delivers these services to help our clients mitigate their risks and vulnerabilities and ensure compliance with FISMA requirements.
As technology constantly transforms at an exponential rate, implementing strategies to keep compliant security measures is imperative. FusionPoint helps meet these demands through our strategy and advisory services. Between our extensive experience in NIST compliance and our team of high caliber FedRAMP advisors, working with FusionPoint Security means achieving quality results in every area of service we provide, including:
-
Advisory Services
– Business case analysis to help determine the cost-benefit justification of achieving FedRAMP certification of your solution
– Establishment of a go-to-market strategy for your cloud products in the federal marketplace
– Assistance with navigating conversations with potential agency sponsors
– Security control implementation analysis, review, and remediation support
– Creation of a roadmap for FedRAMP authorization
– Technical architecture reviews and design support
– FedRAMP security documentation development
– Assistance during 3PAO assessment with artifact collection, interviews, plan of action and milestones (POA&M) development, and documentation updates
-
ISSO Augmentation & Support
– Assessing risks, engaging in continuous monitoring, creating security measures, procedures, and risk management plans, performing security updates, and additional support services depending on specific needs.
-
Continuous Monitoring
– As technology is ever-evolving, continuously monitoring existing security practices is imperative to successfully establishing security. This is achieved through staying apprised of any vulnerabilities and threats to the system on a consistent basis.
-
Security Control Assessment (SCA)
– In the same vein as the need for continuous monitoring, we satisfy security requirements through consistently evaluating security controls to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the information system or organization.
-
Audit Support and Preparation
– We provide comprehensive analyses to evaluate and ensure safety and compliance. Through detecting threats and vulnerabilities, we evaluate the infrastructure to see which systems are up to standard, and what practices need to be implemented to fully optimize the value of an audit.
